THESE HELP REDUCE THE CHANCE OF BEING COMPROMISED
It goes without saying that when we are connected to the
internet we need to pay attention to Security and Privacy.
But we should also practice good digital housekeeping,
especially keeping software updated, ensuring passwords are
unique, 20+ characters, randomly generated, and stored in
a password manager, and not responding to phishing attempts.
FREEZE YOUR CREDIT (now!) -- true piece of mind
Report: Everyone Should Get a Security Freeze
https://krebsonsecurity.com/2015/11/report-everyone-should-get-a-security-freeze/
How I Learned to Stop Worrying and Embrace the Security Freeze
https://krebsonsecurity.com/2015/06/how-i-learned-to-stop-worrying-and-embrace-the-security-freeze/
If you've been paying attention in recent years, you might
have noticed that just about everyone is losing your
personal data. Even if you haven't noticed (or maybe you
just haven't actually received a breach notice), I'm here to
tell you that if you're an American, your basic personal
data is already for sale. What follows is a primer on what
you can do to avoid becoming a victim of identity theft as a
result of all this data (s)pillage.
If you want true piece of mind, freeze your credit file.
How to place or lift a security freeze on your credit report
https://www.usa.gov/credit-freeze
What To Know About Credit Freezes and Fraud Alerts
https://consumer.ftc.gov/articles/what-know-about-credit-freezes-and-fraud-alerts
https://www.aprfinder.com/credit-bureau-phone-numbers
Equifax: 888-548-7878 https://www.equifax.com/
TransUnion: 800-916-8800 https://www.transunion.com/
Experian: 800-493-1058 https://www.experian.com/
Innovis: 800-540-2505 https://www.innovis.com/personal/securityFreeze
MONITOR YOUR FINANCIAL ACCOUNTS (BANKS, etc.)
A checking account is a useful tool for paying bills and
covering expenses when using a debit card. Thanks to online
and mobile banking, it's easier than ever to track debit and
credit transactions.
There are several good reasons to keep a close eye on your
banking activity, particularly if you're concerned about
preventing fraud or minimizing fees.
Monitor all your finances: Bank Accounts, Credit Unions
Accounts, Investment Accounts, and Credit/Debit Card
Transactions. Take advantage of the smartphone apps from
those companies and institutions.
MONITOR YOUR PASSWORDS - Data Breaches Happen
⓵ CHECK IF YOUR PASSWORD HAS BEEN COMPROMISED IN A DATA BREACH
https://haveibeenpwned.com
https://haveibeenpwned.com/Passwords
If your password has been detected in any of these breached
sites -- make sure you login to your account and change the
password. Every password should be unique, 16-20+
characters, randomly generated, and stored in a password
manager.
⓶ CHECK THE INTEGRITY OF YOUR PASSWORDS ON YOUR APPLE DEVICES
https://support.apple.com/en-us/120758
Goto the app: Passwords > Security
iPhone/iPad/Mac can securely monitor your passwords and
alert you if they are weak or appear in known date leaks.
For each flagged password, log into that account and set a
new password. Every password should be unique, 16-20+
characters, randomly generated, and stored in a password
manager.
⓷ USE PASSKEYS INSTEAD OF PASSWORDS
https://support.apple.com/en-us/102195
Passkeys reside on your device, not anywhere else.
Passkeys are a replacement for passwords that are designed
to provide websites and apps a passwordless sign-in
experience that is both more convenient and more secure.
Passkeys are a standard-based technology that, unlike
passwords, are resistant to phishing, are always strong, and
are designed so that there are no shared secrets. They
simplify account registration for apps and websites, are
easy to use, and work across all of your Apple devices, and
even non-Apple devices within physical proximity.
Passkeys are built on the WebAuthentication (or "WebAuthn")
standard, which uses public key cryptography. During account
registration, the operating system creates a unique
cryptographic key pair to associate with an account for the
app or website. These keys are generated by the device,
securely and uniquely, for every account.
One of these keys is public, and is stored on the server.
This public key is not a secret. The other key is private,
and is what is needed to actually sign in. The server never
learns what the private key is. On Apple devices with Touch
ID or Face ID available, they can be used to authorize use
of the passkey, which then authenticates the user to the app
or website.
No shared secret is transmitted, and the server does not
need to protect the public key. This makes passkeys very
strong, easy to use credentials that are highly
phishing-resistant. And platform vendors have worked
together within the FIDO Alliance to make sure that passkey
implementations are compatible cross-platform and can work
on as many devices as possible.
Use passkeys to sign in to apps and websites
https://support.apple.com/guide/iphone/use-passkeys-to-sign-in-to-apps-and-websites-iphf538ea8d0/ios
 YIKES -- IDENTITY THEFT
https://consumer.ftc.gov/topics/privacy-identity-online-security
https://consumer.ftc.gov/topics/identity-theft
https://consumer.ftc.gov/features/identity-theft
https://www.identitytheft.gov
IdentityTheft.gov is the federal government's one-stop
resource for identity theft victims. The site provides
streamlined checklists and sample letters to guide you
through the recovery process.
YIKES -- IDENTITY THEFT
https://consumer.ftc.gov/topics/privacy-identity-online-security
https://consumer.ftc.gov/topics/identity-theft
https://consumer.ftc.gov/features/identity-theft
https://www.identitytheft.gov
IdentityTheft.gov is the federal government's one-stop
resource for identity theft victims. The site provides
streamlined checklists and sample letters to guide you
through the recovery process.

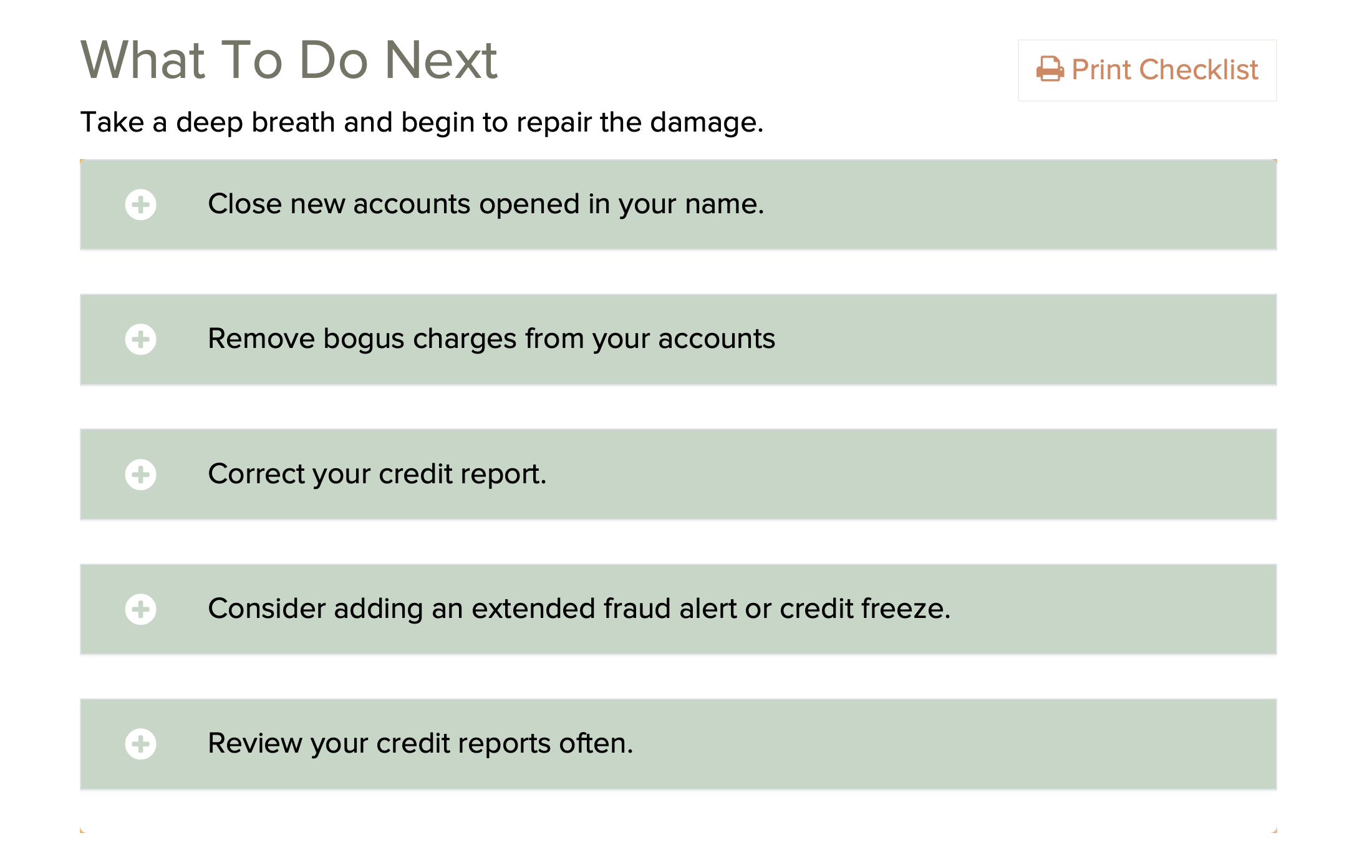
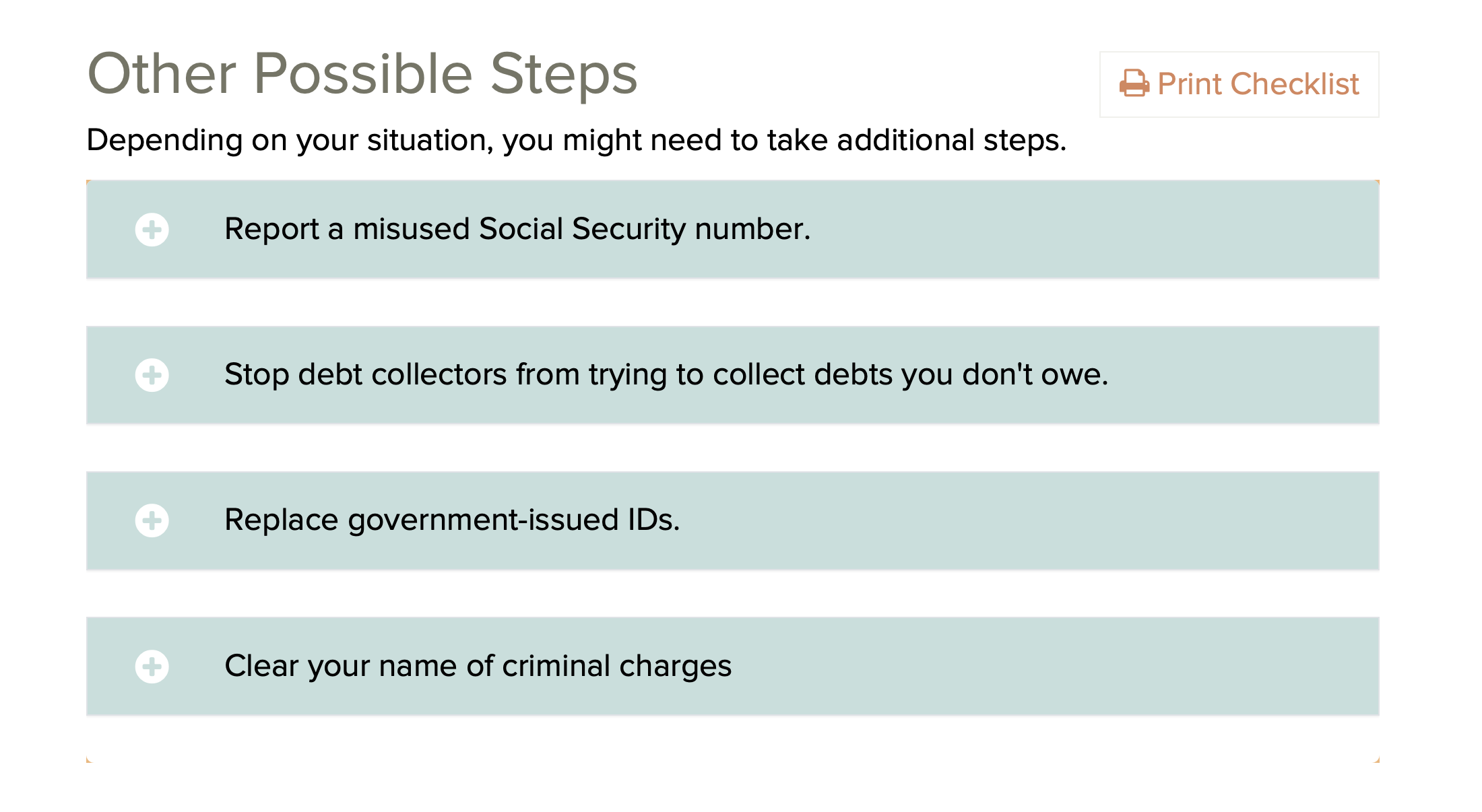


Note: Identity theft insurance, which repays expenses
incurred during identity restoration, is offered by many
insurers as an add-on to existing policies. While some forms
of protection may already be available, individuals should
consider their risk tolerance and the potential long-term
consequences of identity theft before purchasing insurance.
Those who decide to buy should carefully review policy
details, including coverage limits and deductibles.
RESOURCES FROM ELECTRONIC FRONTEER FOUNDATION (EFF)
How to: Avoid Phishing Attacks | Surveillance Self-Defense
https://ssd.eff.org/en/module/how-avoid-phishing-attacks
Protecting Yourself on Social Networks
https://ssd.eff.org/en/module/protecting-yourself-social-networks
Protecting Your Device From Hackers
https://ssd.eff.org/en/module/animated-overview-protecting-your-device-hackers
Tips, Tools And How-Tos For Safer Online Communications
https://ssd.eff.org/en
CISA | NSA | FBI | MS-ISAC
PHISHING GUIDANCE: STOPPING THE ATTACK CYCLE AT PHASE ONE
http://edu-observatory.org/olli/Manage/PDFs/Phishing_Guidance.pdf
Social engineering is the attempt to trick someone into
revealing information (e.g., a password) or taking an action
that can be used to compromise systems or networks. Phishing
is a form of social engineering where malicious actors lure
victims (typically via email) to visit a malicious site or
deceive them into providing login credentials. Malicious
actors primarily leverage phishing for:
1. Obtaining login credentials. Malicious actors conduct
phishing campaigns to steal login credentials for initial
network access.
2. Malware deployment. Malicious actors commonly conduct
phishing campaigns to deploy malware for follow-on activity,
such as interrupting or damaging systems, escalating user
privileges, and maintaining persistence on compromised
systems.
The Cybersecurity and Infrastructure Security Agency (CISA),
National Security Agency (NSA), Federal Bureau of
Investigation (FBI), and Multi-State Information Sharing and
Analysis Center (MS-ISAC) are releasing this joint guide to
outline phishing techniques malicious actors commonly use
and to provide guidance for both network defenders and
software manufacturers. This will help to reduce the impact
of phishing attacks in obtaining credentials and deploying
malware.
The guidance for network defenders is applicable to all
organizations but may not be feasible for organizations with
limited resources. Therefore, this guide includes a section
of tailored recommendations for small- and medium-sized
businesses that may not have the resources to hire IT staff
dedicated to a constant defense against phishing threats.
The guidance for software manufacturers focuses on
secure-by- design and -default tactics and techniques.
Manufacturers should develop and supply software that is
secure against the most prevalent phishing threats, thereby
increasing the cybersecurity posture of their customers.
How to Lose a Fortune with Just One Bad Click
https://krebsonsecurity.com/2024/12/how-to-lose-a-fortune-with-just-one-bad-click/
Summary
Two men, Adam Griffin and Tony, fell victim to a
sophisticated cryptocurrency scam involving phishing emails
and phone calls. The scammers, using a real Google phone
number and a Google Forms email address, convinced the
victims to click on a prompt, granting them access to their
Gmail accounts. This allowed the thieves to drain their
cryptocurrency wallets, with Tony losing 45 bitcoins worth
approximately $4.7 million.
sam.wormley@icloud.com
YIKES -- IDENTITY THEFT https://consumer.ftc.gov/topics/privacy-identity-online-security https://consumer.ftc.gov/topics/identity-theft https://consumer.ftc.gov/features/identity-theft https://www.identitytheft.gov IdentityTheft.gov is the federal government's one-stop resource for identity theft victims. The site provides streamlined checklists and sample letters to guide you through the recovery process.





